If I didn’t know better, I would have thought that the Verified by Visa service offered by arcot.com was a man-in-the-middle attack that was poorly designed to look like a trusted service from Visa (my credit card) and USAA (my bank).
Why your instinct should be to not trust arcot.com
Here’s a few reasons why my instinct was to distrust both Verified by Visa and arcot.com:
- https://secure2.arcot.com/ was not united.com, where I began my purchase
- https://secure2.arcot.com/ was not visa.com, my credit card
- https://secure2.arcot.com/ was not usaa.com, my bank
- https://secure2.arcot.com/ was asking for personal information (name, credit card secuirty code, expiration date, and birth date) that I had already provided united.com
- https://secure2.arcot.com/ has an unprofessional text-only website that reads “This is Secure2.arcot.com. This is the Arcot OBO verified by visa service. Please visit visa website for more details.” Notice it has no outgoing links, so no referrals traffic would be noticed by visa.com
- https://www.arcot.com/ doesn’t exist and displays an SSL Connection Error (error 107)
- https://www.arcot.com/ automatically redirects you to https://www.ca.com/us/multifactor-authentication.aspx, which is yet another party
- USAA’s website has no mention of arcot.com
- Visa’s website has a few mentions of arcot.com buried in PDF documents
- United’s website has no mention of arcot.com
Why Verifed by Visa and arcot.com looked like a man-in-the-middle attack
A MITM attack requires that the attacker place himself between two parties that are trying to communicate (me and united.com) and impersonate at least one of the parties (look like Visa or USAA). The arcot.com site required me to enter my name, the three-digit security code on the back of my Visa, the expiration date of my card, and my birth date — all of which was information that I already provided to united.com.
arcot.com has a very weak password policy
I knew arcot.com was legit even though it’s behavior is quite suspect. I believe a newegg.com purchase first exposed me to this process. But this time, arcot.com required me to create a password for their service.
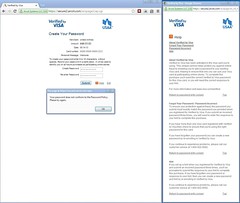 Their password requirement reads: “To create your password enter 6 to 10 characters, without spaces.” But each time I entered a password, it would get rejected by this message: “Your password does not conform to the Password Policy. Please try again.” The is no link to a Password Policy and the link to Help does not contain information about their password policy.
Their password requirement reads: “To create your password enter 6 to 10 characters, without spaces.” But each time I entered a password, it would get rejected by this message: “Your password does not conform to the Password Policy. Please try again.” The is no link to a Password Policy and the link to Help does not contain information about their password policy.
Here are the five passwords I attempted:
- hup52!eChu
- XeW=A#rA5&
- #re_aqeS7s
- 4racrE$rec
- beNu&Em9fu
Each of which is between 6 to 10 characters and would take a desktop PC about 58 years to crack). What ended up working was a much weaker alpha-numeric 10-character password that would take a desktop PC about 6 years to crack. That was the best level of security Verified for Visa and arcot.com afforded me.
Password limits imply poor security
Restricting users to a small selection of characters and a length of 6 to 10 characters gives the impression that arcot.com is storing user-entered passwords in an insecure form (like plain text).
The best practice for collecting and storing user submitted passwords is to:
- Permit any character (entropy)
- Permit an unlimited number of characters (length)
- Add salt (unique random data added to each user’s password)
- Hash the user password with appended salt (algorithm to change variable length data to a fixed length)
- Re-hash several times (fixed is fine, but random per user would be better)
- Store the final hash in an encrypted database, the unique-per-user salt in a separate encrypted database, and the random-number-of-hashes-per-user in a third encrypted database — each database on separate systems with separate credentials
Because arcot.com limits me to 10 alpha-numeric characters, I’m given the uneasy impression that they do not hash my password. If they did hash my password they would not care if I put in 20 characters or 2,000 characters, the hash would produce the same 256-character result (regarding length).
Shame on United, Visa, and USAA
Shame on the three of you for working with a third-party service that looks like a man-in-the-middle attack. I applaud you for wanting to improve your security and reduce online fraud, but this implementation is terrible and leads me to question your priority for security.
If you want to increase a security layer, do so from your own sites (which we trust) and not from a website we’ve never heard of. Use of subdomains would be fine. Additionally, permit users to enter very long and very complex passwords. Tools like LastPass automate this process.
Visa and banks in particular need to be vigilant in teaching their customers how to be secure and then practice what they preach. USAA has published several articles about online security and should be ashamed for having any connection to arcot.com’s Verified By Visa implementation.
I found this page because my instinct was to distrust Arcot Systems, for exactly the reasons you have outlined. I completely agree that this is shoddy work that, as a professional software developer, I would be ashamed to call mine.
Same experience, an attempted purchase at one site already has my CC details yet leads me to Arcot site and ask much the same questions and more (DOB).
The relationship between these sites and my card issuing bank and CC provider may be valid, but there is no way in the world I’m giving my details to this dodgy attempt.
I completely agree. There is not even a cancel button on the page and as far as I am aware no payment has gone through. Needed to contact the seller / website owner to arrange payment over the phone or bank transfer if necessary. If any it is training innocent customers to ignore all these warning signs. DODGY
I agree with you guys. This thing is Kafkan. I still can’t make changes to my flight because the United form keeps kicking out my CVVC number. When the United page ran the little notice about using Arcot or else maybe get held up at payment time, I decided to get my password now. Talk about torture; you’re typing in numbers that you can’t see, and so are making all kinds of errors without knowing what they are. After several tries (I’m 75 and don’t have complete control of my fingers) Apcot told me to get lost. I don’t know if Apcot had any role in screwing up United’s handling of my CVVC number, and I don’t know if I’ll be able to complete the flight change without jumping through the Apcot hoops. Plus I’m out of the country and can’t phone United.
I guess I’ll have my 80-year-old husband and my 63-year-old neighbor in Texas make the phone call to United for me. Curse the airlines.
Yeah, I was just trying to make a purchase off new egg as well and many of these exacts thought, both about the redirect being suspect and the ridiculous password policy. I shouldn’t be forced to use a less secure password for something linked directly to my credit card and why doesn’t a service being called ‘verified by Visa’ go through visa.com, either that or call it ‘verified by arcot’ so at least it does seem deceptive.
I totally agree this is a dangerous practice – ‘training’ customers to reveal much of personal information to the man in in middle – even to a legit one. It shakes my confidence in the VISA system itself – they should not allow schemes like this one.
An automatic email or SMS notification about credit card transactions is much better protection against fraud.
Totally agree with others. Poor design and domain choice for a verification system like this.
This comes up when I try to make a purchase. It did seem a bit shady. So would it be alright if I filled everything out and completing my purchase? Last time I tried that my account was frozen.