This evening I mistyped a URL and was redirected to https://virus–alert–warning.com/warning_error.dill (I changed the link to go to a security article).
This URL, its error message, and its phone number is a scam. No harm has occurred to your computer and you should not call the number. Simply force your browser to close via Task Manager, or perform a reboot.
Your Action
I recommend that you…
- Do not call the phone number
- Attempt to close your browser
- (or) Open Task Scheduler and attempt to force your browser to close
- (or) Reboot your computer
Screen Shots of the Scam
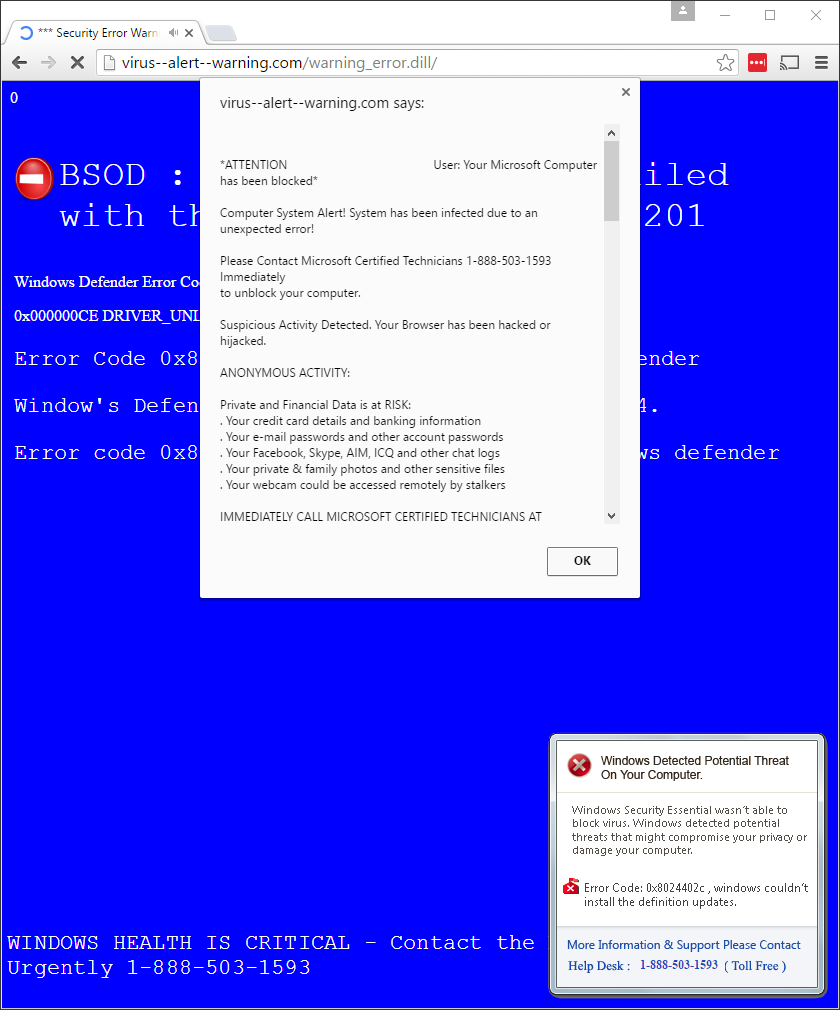
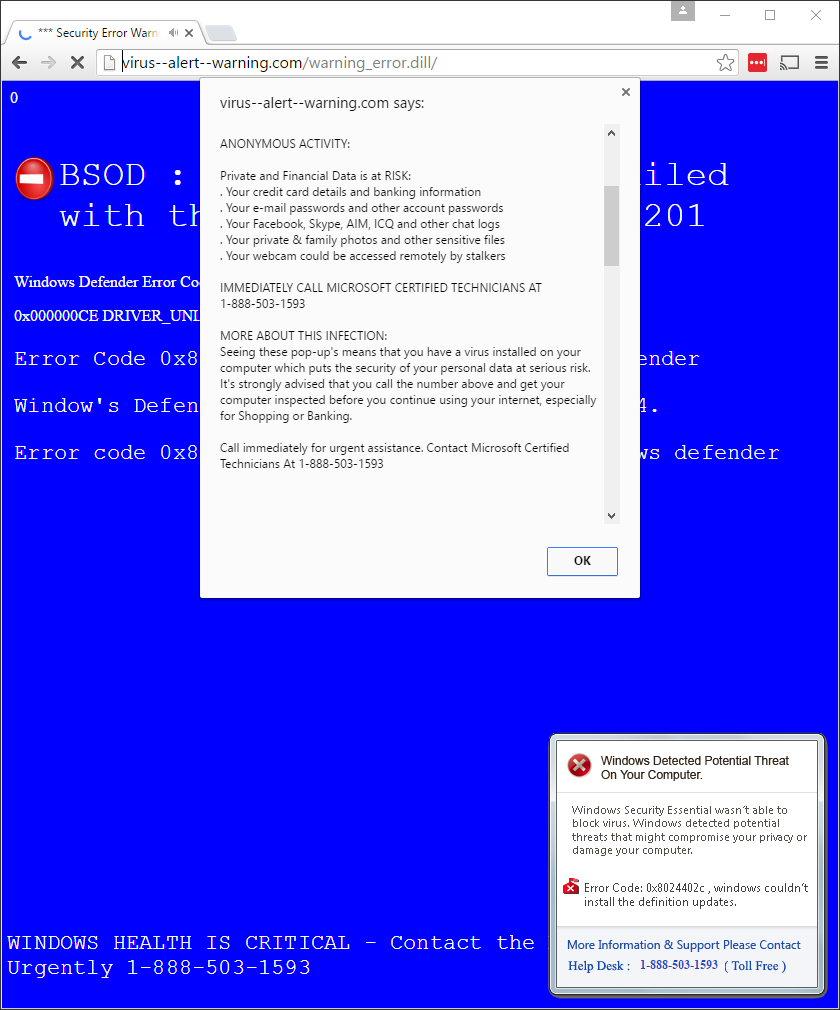
The scam in action.
Screen Shots of the Scam’s HTML source code
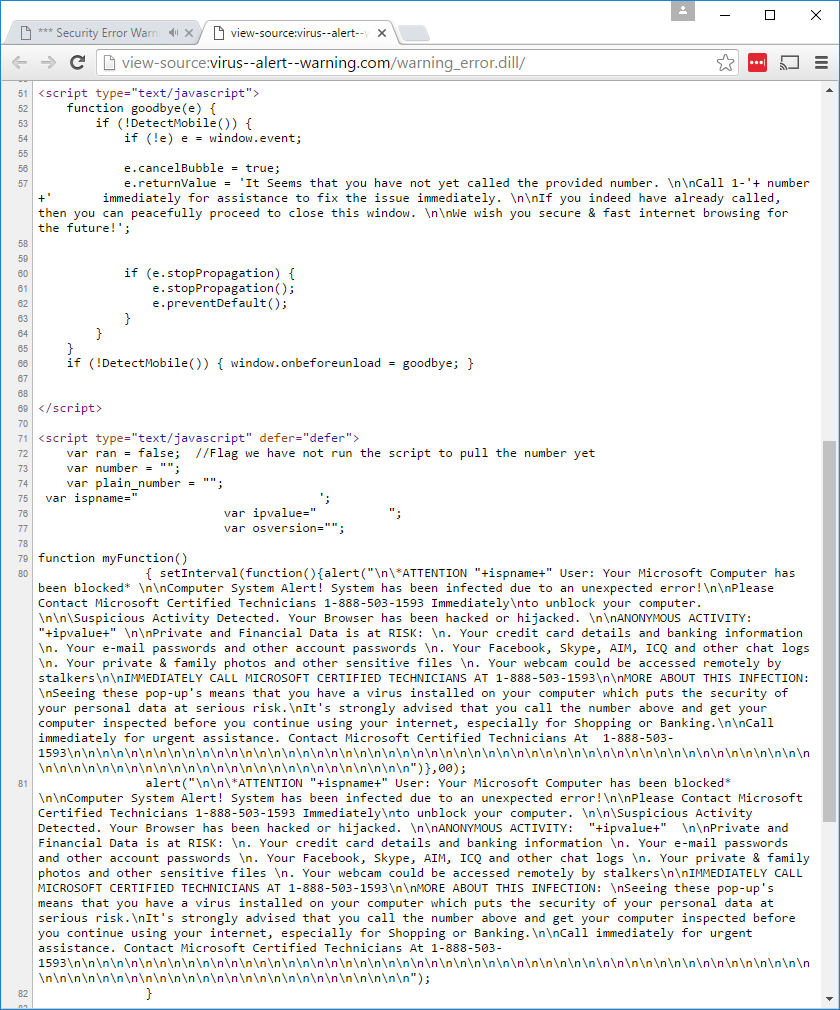
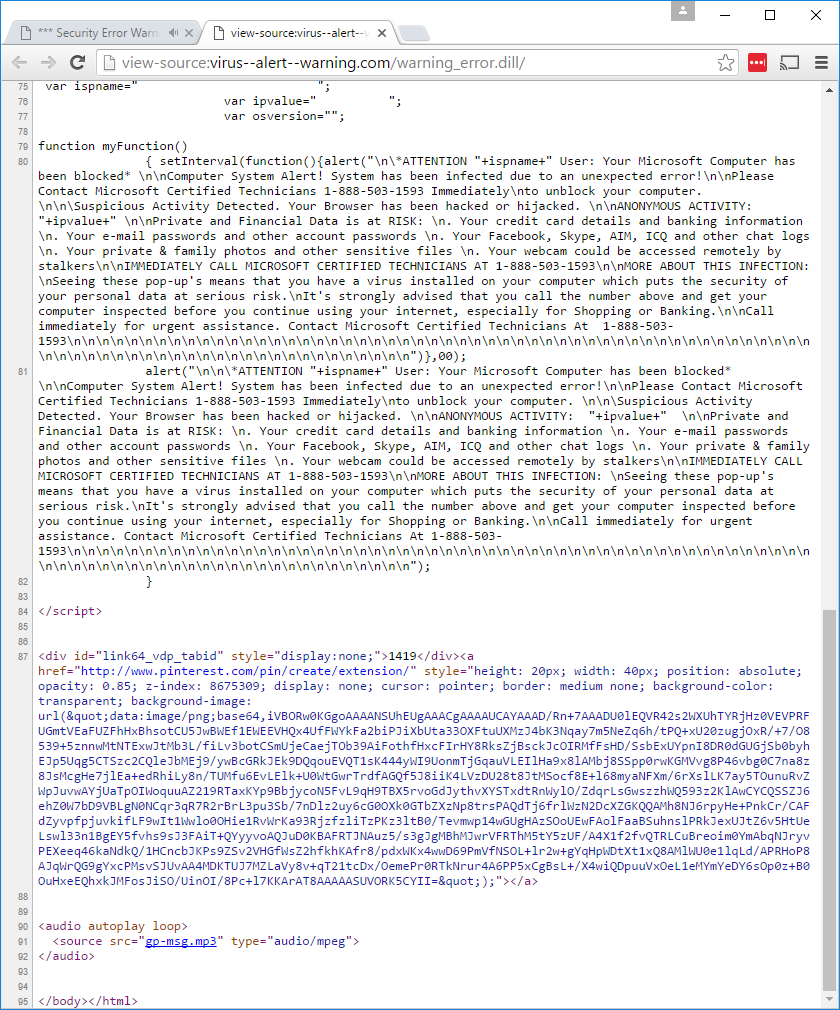
The source code used to create the scam.

Text from the scam’s popup
The content of the popup window.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 | ATTENTION User: Your Microsoft Computer has been blocked Computer System Alert! System has been infected due to an unexpected error! Please Contact Microsoft Certified Technicians 1-888-503-1593 Immediately to unblock your computer. Suspicious Activity Detected. Your Browser has been hacked or hijacked. ANONYMOUS ACTIVITY: Private and Financial Data is at RISK: Your credit card details and banking information Your e-mail passwords and other account passwords Your Facebook, Skype, AIM, ICQ and other chat logs Your private & family photos and other sensitive files Your webcam could be accessed remotely by stalkers IMMEDIATELY CALL MICROSOFT CERTIFIED TECHNICIANS AT 1-888-503-1593 MORE ABOUT THIS INFECTION: Seeing these pop-up's means that you have a virus installed on your computer which puts the security of your personal data at serious risk. It's strongly advised that you call the number above and get your computer inspected before you continue using your internet, especially for Shopping or Banking. Call immediately for urgent assistance. Contact Microsoft Certified Technicians At 1-888-503-1593 |
Text from the scam’s blue webpage
The content of the blue webpage.
1 2 3 4 5 6 7 8 9 10 11 12 13 | BSOD : DllRegisterServer failed with the error code 0x80040201 Windows Defender Error Code: 0x80073afc 0x000000CE DRIVER_UNLOADED_WITHOUT_CANCELLING_PENDING_OPERATIONS Error Code 0x800705b4 when Starting Windows Defender Window's Defender Time Out Error code 0x800705b4. Error code 0x800705b4 when trying to open windows defender WINDOWS HEALTH IS CRITICAL - Contact the Microsoft Help Desk Urgently 1-888-503-1593 |
Source code of the scam’s blue webpage
The HTML code used to create the blue page and popup.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 | <!DOCTYPE html>
<html>
<head>
<meta content="text/html; charset=utf-8" http-equiv="Content-Type">
<title>*** Security Error Warning 0x80070424</title>
<link href="error0x80070424_files/style.css" rel="stylesheet" type="text/css">
<script>
function getURLParameter(name) {
return decodeURI(
(RegExp(name + '=' + '(.+?)(&|$)').exec(location.search)||[,null])[1] || ''
);
}
</script>
<script>
function DetectMobile() {
if (/Android|webOS|iPhone|iPad|iPod|BlackBerry|IEMobile|Opera Mini/i.test(navigator.userAgent)) { return true; } else { return false; }
}
if (DetectMobile()) { document.body.style.backgroundImage = 'none' }
</script>
</head>
<body data-pinterest-extension-installed="ff1.35" onload="myFunction();">
0
<table align="center" border="0" cellpadding="2" cellspacing="2" width="100%">
<tbody>
<tr>
<td height="100%" style="padding-top:10px;">
<p class="style2"><img height="46" src="error0x80070424_files/url.png" style="float:left;" width="45">BSOD : DllRegisterServer failed with the error code 0x80040201</p>
<p class="style5">Windows Defender Error Code: 0x80073afc</p>
<p class="style5">0x000000CE DRIVER_UNLOADED_WITHOUT_CANCELLING_PENDING_OPERATIONS</p>
<p class="style4">Error Code 0x800705b4 when Starting Windows Defender</p>
<p class="style4">Window's Defender Time Out Error code 0x800705b4.</p>
<p class="style4">Error code 0x800705b4 when trying to open windows defender</p>
<p class="style6"> </p>
<p class="pbotm">WINDOWS HEALTH IS CRITICAL - Contact the Microsoft Help Desk Urgently <span id="FormattedNumber1">1-888-503-1593</span></p>
<div style="position: absolute; right:120px; bottom:35px; z-index: 9">
<span id="FormattedNumber2" style="color: #164abe; font-size: 12px; font-weight: bold">1-888-503-1593</span>
</div><img height="284" src="error0x80070424_files/alert-2.png" style="position: absolute; right:5px; bottom:5px;" width="298">
</td>
</tr>
</tbody>
</table>
<script type="text/javascript">
function goodbye(e) {
if (!DetectMobile()) {
if (!e) e = window.event;
e.cancelBubble = true;
e.returnValue = 'It Seems that you have not yet called the provided number. \n\nCall 1-'+ number +' immediately for assistance to fix the issue immediately. \n\nIf you indeed have already called, then you can peacefully proceed to close this window. \n\nWe wish you secure & fast internet browsing for the future!';
if (e.stopPropagation) {
e.stopPropagation();
e.preventDefault();
}
}
}
if (!DetectMobile()) { window.onbeforeunload = goodbye; }
</script>
<script defer="defer" type="text/javascript">
var ran = false; //Flag we have not run the script to pull the number yet
var number = "";
var plain_number = "";
var ispname="Comcast Networks Llc";
var ipvalue="50.9.7.30";
var osversion="";
function myFunction()
{ setInterval(function(){alert("\n\*ATTENTION "+ispname+" User: Your Microsoft Computer has been blocked* \n\nComputer System Alert! System has been infected due to an unexpected error!\n\nPlease Contact Microsoft Certified Technicians 1-888-503-1593 Immediately\nto unblock your computer. \n\n\Suspicious Activity Detected. Your Browser has been hacked or hijacked. \n\nANONYMOUS ACTIVITY: "+ipvalue+" \n\nPrivate and Financial Data is at RISK: \n. Your credit card details and banking information \n. Your e-mail passwords and other account passwords \n. Your Facebook, Skype, AIM, ICQ and other chat logs \n. Your private & family photos and other sensitive files \n. Your webcam could be accessed remotely by stalkers\n\nIMMEDIATELY CALL MICROSOFT CERTIFIED TECHNICIANS AT 1-888-503-1593\n\nMORE ABOUT THIS INFECTION: \nSeeing these pop-up's means that you have a virus installed on your computer which puts the security of your personal data at serious risk.\nIt's strongly advised that you call the number above and get your computer inspected before you continue using your internet, especially for Shopping or Banking.\n\nCall immediately for urgent assistance. Contact Microsoft Certified Technicians At 1-888-503-1593\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n")},00);
alert("\n\n\*ATTENTION "+ispname+" User: Your Microsoft Computer has been blocked* \n\nComputer System Alert! System has been infected due to an unexpected error!\n\nPlease Contact Microsoft Certified Technicians 1-888-503-1593 Immediately\nto unblock your computer. \n\n\Suspicious Activity Detected. Your Browser has been hacked or hijacked. \n\nANONYMOUS ACTIVITY: "+ipvalue+" \n\nPrivate and Financial Data is at RISK: \n. Your credit card details and banking information \n. Your e-mail passwords and other account passwords \n. Your Facebook, Skype, AIM, ICQ and other chat logs \n. Your private & family photos and other sensitive files \n. Your webcam could be accessed remotely by stalkers\n\nIMMEDIATELY CALL MICROSOFT CERTIFIED TECHNICIANS AT 1-888-503-1593\n\nMORE ABOUT THIS INFECTION: \nSeeing these pop-up's means that you have a virus installed on your computer which puts the security of your personal data at serious risk.\nIt's strongly advised that you call the number above and get your computer inspected before you continue using your internet, especially for Shopping or Banking.\n\nCall immediately for urgent assistance. Contact Microsoft Certified Technicians At 1-888-503-1593\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n\n");
}
</script>
<div id="link64_vdp_tabid" style="display:none;">
1419
</div><a href="https://www.pinterest.com/pin/create/extension/" style="height: 20px; width: 40px; position: absolute; opacity: 0.85; z-index: 8675309; display: none; cursor: pointer; border: medium none; background-color: transparent; background-image: url("data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAACgAAAAUCAYAAAD/Rn+7AAADU0lEQVR42s2WXUhTYRjHz0VEVPRFUGmtVEaFUZFhHxBhsotCU5JwBWEf1EWEEVHQx4UfFWYkFa2biPJiXbUta33OXFtuUXMzJ4bK3Nqay7m5NeZq6h/tPQ+xU20zugjOxR/+7/O8539+5znnwMtNTExwJtMb3L/fiLv3botCSmUjeCaejTOb39AiFothfHxcFIrHY8RksZjBsckJcOIRMfFsHD/SsbExUYpnI8DR0dGUGjSb0byhEJp5Uqg5CTSzc2CQleJbMEj9/ywBcGRkJEk9DQqouEVQT1sK444yWI9UonmTjGqauVLEIlHa9x8lAMbj8SSpp0rwKGMVvg8P46vbg0C7na8z8JsMcgHe7jlEa+edRhiLy8n/TUMfu6EvLElk+U0WtGwrTrdfAGQf5J8iiK4LVzDU28t8JtMSocf8E+l68myaNFXm/6rXslLK7ay5TOunuRvZWpJuvwAYjUaTpOIWoquuAZ219RTaxKYp9BbjycoN5FvL9qH9TBX5rvoGdJythvXYSTxdtRnWylO/ZdqrLsGwszzhWQ593z2KlAwCYCQSSZJ6ehZ0W7bD9VBLgN0NCqr3qR7R2rBrL3pu3Sb/7nDlz2uy6cG0OXk0GTbZXzNp8trsPAQdTj6frlWzN2DcXZGKQQAMh8NJ6rpyHe+PnkCr/CAFdZyvpfpjuvkifLF9wIt1Wwlo0OHie1RvWrKa93RjzfzliTzPKz3ltB0/Tevmwp14wGUgHAzSOoUEwFAolFaaBSuhnslPRkJexUJtZ6v5HtUeLswl33n1BgEY5fvhs9sJ3FAiT+QYyyvoAQJuD0KBAFRTJNAuz5/s3gJgMBhMJwrVFRThM5tY5zUF/A4X1f2fvQTRLCuBreoim0YmAbqNJryvPEXeeq46kaNdkQ/1HCncbJKPs9ZSv2VHGfWsZ2hfkhKAfr8/pdxWKx4wwD69PmVfNSOL+lr2w+gYqHpWDtXt1xQ8AMlWU0e1lqLd/APRHoP8AJqWrQG9gYxcPMsvSJUvAA4MDKTUJ7MZLaVy8v+qT21tcDx/OemePr0RTkNrur4A6PP5xCgBsL+/X4wiQDpuuVxOeL1eMYmYeDY6sOp0z+B0OuHxeEQhxkJMFosJiSO/UinOI/8Pc+l7KKArAT8AAAAASUVORK5CYII=");"></a> <audio autoplay="" loop=""><source src="gp-msg.mp3" type="audio/mpeg"></audio>
</body>
</html> |
